How Disposition Works For iPhone Cases Stolen Device
When an iPhone is reported as lost or stolen, it essentially becomes married to the owner’s Apple ID and difficult for anyone else to use. This aspect of safety is mainly encompassed by Apple’s “Find My” service and the Stolen Device Protection feature, increasing protection levels for a device.
Device Locking Mechanism
Lost Mode: When a device is marked as Lost in the app or Find My on iCloud. When left in this state, the iPhone is all locked up with the user’s passcode and accessing Apple Pay will be impossible. As a result, even if lost or stolen, the device becomes useless in the absence of owner’s credentials.iPhone security (ad) The Lost Mode will also give the owner a way to display a contact number on their lock screen, potentially providing an opportunity for whoever finds it to be able to return it.
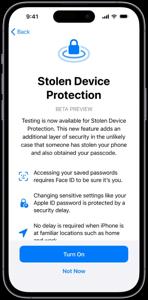
Stolen Device Protection
Announced with iOS 17.3, Stolen Device Protection is another security feature. No outside critical actions means biometric authentication (Face ID or Touch ID) This even implies that if a thief knew the passcode, besides he had biometrics to authenticate himself in order to change account setting or disable the Lost mode. Added measures is that some operations has a security delay measure before user can claim his/her account making it safer from unauthorized access.
Reporting and Recovery Steps
If stolen, individuals should report the theft to local law enforcement and their wireless carrier immediately, so service can be shut off and claims possibly filed. You must also change the Apple ID password at once in order to secure personal data. Assuming the device is not recoverable, users will also be able to remotely erase their iPhone and have it remain associated with their Apple ID for future tracking efforts.
So in conclusion, an iPhone stolen can be made useless to unauthorized users because of its close ties with Apple ID and the many security features offered by it; but only when the owner acts promptly.
